I recently gave a talk on how DNS can be used for malware command and control and data exfiltration and in particular how DNS creates an exploitable hole in your firewall.
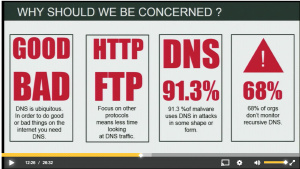
The talk was aimed at a mixed audience so I didn’t get chance to deep dive into the technical details but what I did cover was the more high level concepts on DNS-based covert channels and their detection. In the talk I examine two pieces of malware that show that DNS is targeted as a means of malware communication and has been used in the past as a data exfiltration channel. Recent security industry reports have suggested that 90+% of malware uses DNS, which is not surprising given that almost every other Internet activity is dependant on DNS. From a firewall security point of view the focus is often on payload heavy protocols such as HTTP and FTP so it is not uncommon for DNS traffic to get a free rein.
 Detecting DNS-based channels is not that difficult and in fact most of the standard tools that are freely available can be easily fingerprinted and detected once you know what to look for. However, there is anecdotal evidence to suggest that many organisations do not log DNS traffic and therefore have no idea of what is “normal” DNS activity for their organisation.
Detecting DNS-based channels is not that difficult and in fact most of the standard tools that are freely available can be easily fingerprinted and detected once you know what to look for. However, there is anecdotal evidence to suggest that many organisations do not log DNS traffic and therefore have no idea of what is “normal” DNS activity for their organisation.
Logging DNS traffic can bring about its own problems in terms of privacy, impact of services and data storage. In the linked video I talk about a number of ways in which organisations can begin to investigate DNS activity without having to pay a heavy price in terms of resources and DNS server responsiveness.
There is a lot of “security intelligence” to be gained from analysing DNS traffic and in my own view it is something that all organisations should do on a frequent basis.